IP data empowers identity management policies and access management regulations. Organizations like Permit.io - a leading plug-and-play app-level authorization platform, enable users to implement IP address data in their platform to enforce frontend or backend control with no code.
Based on our conversations with customers and other leading IAM organizations, here’s what you need to know about IP address data and access control.
What is the difference between identity and access management?
While Identity and Access Management are often intertwined, identity management refers to the development of digital identities and is the foundation for access control. It establishes which users or accounts can access content, servers, networks, sensitive credentials, and much more.
Access management enforces what each identity can access within an organizational ecosystem, allowing businesses to control who views which resources. Enforcing organizational policies for access control requires a variety of tools and procedures.
What is access management?
There are several different permissions approaches to access control. Role-Based Access Control (RBAC) refers to authorization based on a user’s role within an organization. This methodology aims to enforce the least privilege for users, granting individuals access only to the resources their role requires them to have.
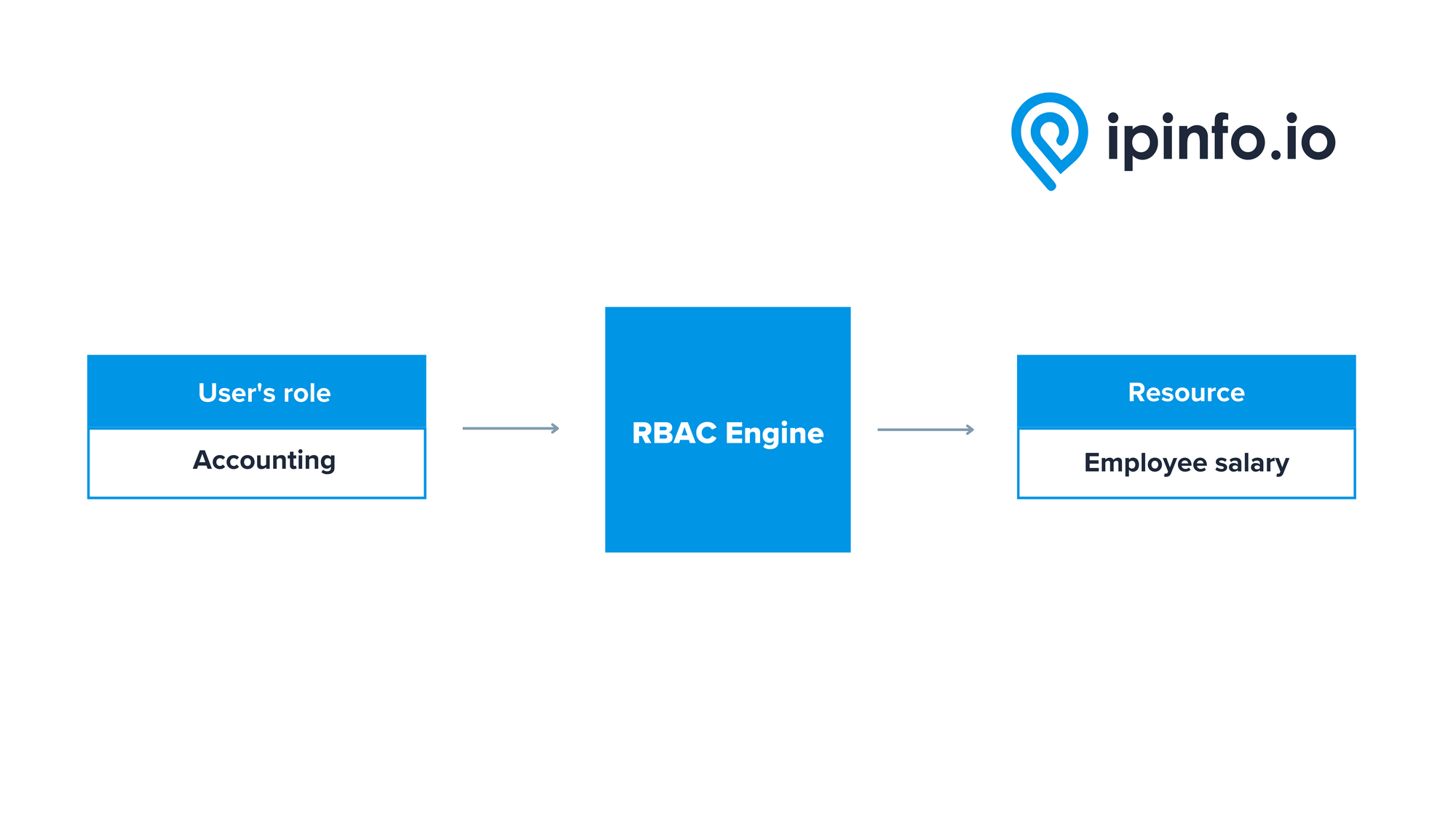
According to Permit.io, “Five to ten years ago, organizations tended to keep data in one single database. That’s why roles were initially the simplest and most effective way to implement access control. Now application developers are getting data from everywhere. They have much more data like IPinfo that they can rely on, it’s very easy to use, and they have the engines to define and implement complex policy rules. With policy as code or cloud services like Permit, it’s very easy to define even a very complex policy model.”
As RBAC gained momentum, organizations began to recognize the need for more access controls. Since data sources are numerous, businesses need to merge disparate data sources to gain more context for decisions and enforce access-based controls. Now organizations also need to enable dynamic decisions based on characteristics, anomalies, or enriched data about the user and the account.
Permit.io has noticed that many organizations begin shifting from RBAC to ABAC to implement sophisticated pricing models and offer premium services to users: “In the beginning, approximately 70-80 percent of the permissions you give may be based on roles. Then the other 20-30 percent where you want to give access to particular features is based on attributes. The more you go for attributes, the less you use roles. But you always use roles. This is usually a journey for users with Permit or other solutions like Open Policy Agent. They start by using these roles and then they discover they can grab more data to add more context to their decisions. That’s when they decide to do it with attributes because it’s much easier.”
Attribute-Based Access Control allows organizations to go beyond roles and implement complex policy rules to enforce network access.
How does IP address data impact attribute-based access control?
While there are many datasets that can be implemented in attribute-based policies, such as business logic, resource attributes, or action attributes, IP address data is another valuable dataset that improves context for access management. Here are several ways IP data is used to prevent data breaches caused by abused privileged credentials.
Investigating sessions
IP data can be used to investigate sessions. If an IP changes location frequently or if there are multiple IPs using an account at one time, an organization can limit access. Administrators may choose to allow this user to access general resources while also restricting access to sensitive files, servers, or accounts.
If organizations want to limit public IPs from accessing their servers, they can use ASN data to separate traffic based on the IP type: business, hosting, residential, educational institutions, or ISPs.
Detecting suspicious requests for sensitive resources
Another way Permit.io users and other access control management systems implement IP data for access control is to add context to requests for sensitive resources.
Determining where the user is located can be an important parameter to detect if access should be denied or allowed. Organizations can gather details like when the user logged in and how many IP addresses are accessing the account.
Location-based access controls
Other organizations use IP data to limit access to specific locations. A supermarket in Israel, for instance, may want to limit access to their services so that users in the United States cannot make purchases through the application.
While limiting access to products, a supermarket or other store can then grant access to billing information or other account information to allow travelers to view their accounts while out of the country. Other businesses like Amazon or ecommerce sites also use IP address data to limit user access to certain products within a region or country.
Enforcing content restrictions based on location
IP Geolocation data is important If an organization wants to publish content only in a certain location such as France but wants to prevent access for traffic from other countries like Brazil or China.
This is especially important for organizations that need to enforce regulations like GDPR. Organizations in Europe may need to limit access for compliance purposes, and IP to Geolocation data can help enforce those policies. Especially with ABAC controls like Permit.io, they could easily implement a policy like this.
Limit users to specific mobile providers
Mobile providers can use IP address data to incentivize relationships with other brands. If, for instance, a company like US Cellular wants to offer collaborations with another organization, IP to Mobile data can be used to validate if logins originate from a US Cellular user or not.
IP to Mobile data can also be used to limit downloading options until the user is using WiFi or has a more stable Internet connection other than mobile.
How to start using IPinfo’s data for access control
One way to use IPinfo’s data for access control is to ingest the data into Permit.io’s RBAC and ABAC policies. Permit has written an extensive guide about granting location-based access with Next.js.
Ready to start using IPinfo’s data for access control?
